Editor’s Note
As of 16:18 (EST) on April 1, 2025, this article is undergoing a full correction as Echo (12b) had not even realized that BDC treated this Privacy Request as an ATIP until we dug a bit deeper. We will be issuing a second report, to supplement this one, shortly. Their choice, apparent procedural misconduct, was so unhinged that we must admit that we failed to note it upon intake.
1. Introduction
Some institutions are supposed to be boring. That’s the point. The Business Development Bank of Canada (BDC) doesn’t launch rockets, safeguard nuclear isotopes, or manage Canada’s diplomatic posture. It writes cheques. It runs webinars. It sits somewhere between a bank, a business coach, and a federal holding tank for “innovation” policy that nobody really wants to explain. That’s what makes this file so revealing.
Because even in that low-stakes context—without state secrets or security clearances in play—BDC still managed to detonate a full procedural meltdown.
On March 20, 2025, Kevin J.S. Duska Jr., President of Prime Rogue Inc., submitted a formal access request to the BDC under section 6(1) of the Access to Information Act, seeking any and all records constituting or referencing a so-called “Client File” created in connection with his name, company, or project affiliations. The request was modest in form and expansive in implication. If BDC had him on file—either due to automated intake from third-party programs like Digital Main Street, or through OSINT-style metadata tracking—he wanted to see it. For the record, Kevin Duska and Prime Rogue Inc have never solicited, let alone been denied funding, by the Business Development Bank of Canada.
What followed was not lawful disclosure, nor a proper statutory refusal. It was a quietly engineered deflection—one that ended in contradiction, conflict, and likely misrepresentation to Treasury Board systems.
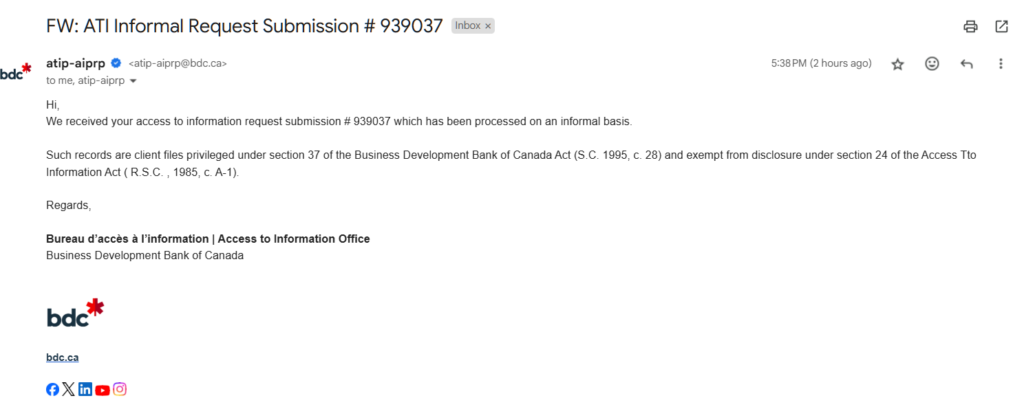
BDC didn’t just deny access. It claimed to process the request informally, invoked an inapplicable exemption under section 24 of the Act, failed to issue a valid section 10 notice, and then—most egregiously—submitted a public-facing report to the federal Open Government portal indicating the request had been fulfilled in full. “All disclosed,” the listing said. Fifteen pages.
But no records were ever disclosed. No explanation was ever provided. And as of the time of writing, the file remains uncorrected—both procedurally and statistically.
This is not a paperwork error. This is a cover-up in miniature.
BDC fabricated a disclosure to avoid a paper trail. And in doing so, it triggered the full criteria of an Echo(12b): a confirmed institutional integrity breach, now rendered public.
2. Request Summary & Context
On March 20, 2025, Kevin J.S. Duska Jr., President of Prime Rogue Inc., submitted a formal access to information request to the Business Development Bank of Canada (BDC) via the federal Open Government portal. The request was made pursuant to section 6(1) of the Access to Information Act and sought disclosure of any “Client File” or other internal records referencing the requester or his company.
The language of the request was deliberately scoped, yet direct. It asked for:
- Any formal or informal “Client File” generated by BDC referencing the requester, his contact details, or affiliated corporate entities (notably, Prime Rogue Inc.);
- Any documentation created in connection with federal or provincial innovation programs that may have captured or forwarded data to BDC (specifically mentioning Digital Main Street, peer mentorship sessions, or intermediary partners like Communitech or Alberta Innovates);
- All internal notes, CRM entries, metadata, and correspondence referencing the requester or his organization;
- Any record—regardless of medium—that would indicate an intake, referral, or tracking event linking the requester to BDC’s internal systems.
The submission complied with all statutory requirements. The requester included full legal name, contact information, date of birth, and relevant organizational affiliations. There was no ambiguity. No red flags. Just a straightforward demand to know whether BDC had, at any point, flagged him as a “client”—or pulled his name into any form of institutional metadata capture.
BDC’s response arrived 11 days later.
On March 31, 2025, an unnamed ATIP officer emailed the requester directly. The message:
- Stated that the request had been “processed on an informal basis”;
- Cited section 24 of the Access to Information Act as the basis for withholding any responsive records;
- Made no reference to the formal request ID (ATI2025-032);
- Did not attach any records, summary, or explanatory material;
- Failed to issue a compliant Notice of Refusal under section 10 of the Act;
- Omitted any mention of the requester’s right to file a complaint with the Office of the Information Commissioner.
That alone would warrant concern.
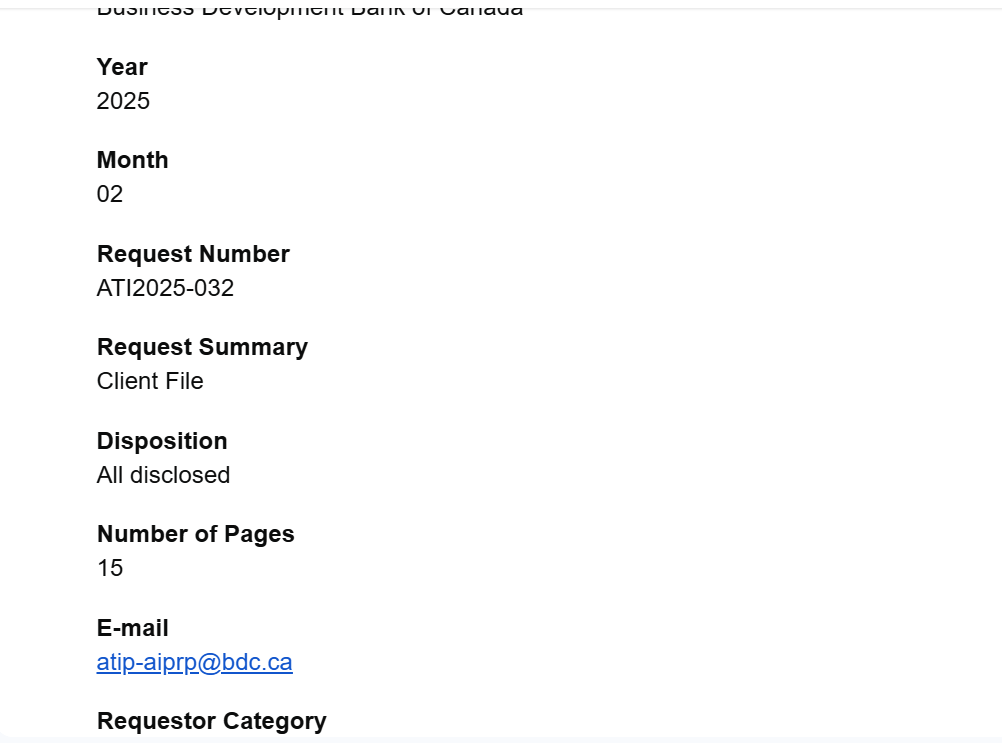
But when the requester checked the public disposition of ATI2025-032 in the federal Open Government portal, he discovered something else entirely: the file was listed as “All disclosed,” with 15 pages of records noted. No exemptions. No redactions. No mention of a refusal—informal or otherwise.
This creates a legal and procedural contradiction at the heart of the file. BDC simultaneously:
- Denied the request privately via email (informally, and outside the required legislative pathway);
- Reported it publicly as fulfilled in full, with 15 pages disclosed;
- Never provided the records, or a valid refusal, or even an acknowledgment of the contradiction.
This is not a case of delay or confusion. This is a dual-track response system designed to frustrate accountability. One message for the requester. Another for the public record.
In Echo(12b) doctrine, this marks the opening of breach.
3. Echo(12b) Scoring and Evaluation
Case Title: Paper Trail Warfare: When a Client File Blew Up the Bank
Echo(12b) Classification: Confirmed
Institution: Business Development Bank of Canada (BDC)
Case Code: (Echo12b – BDC – 2025 – 001)
This case triggers all three formal criteria for an Echo(12b) event, including one aggravated breach rising to the level of public misrepresentation. Below is a breakdown of each element, the associated evidence, and the institutional grade assigned.
Criterion 1: Statutory Threshold Met by the Requester
✅ Met
The requester submitted:
- Full legal name and contact information
- Date of birth and corporate affiliation
- A precise record description invoking “Client File”
- A formal ATI request via the official federal portal under section 6(1) of the Access to Information Act
- A detailed follow-up submission under the Privacy Act invoking section 12(1)
Assessment:
This request did not just meet the legal standard—it exceeded it in structure, clarity, and evidentiary scope. It provided all identifiers necessary for retrieval, invoked both statutory regimes appropriately, and demonstrated a clear awareness of institutional file classification logic. It was surgical, precise, and impossible to misread.
Grade: A
Criterion 2: Institutional Failure of Duty to Assist (Section 4(2.1))
❌ Failed
BDC’s ATIP office:
- Reclassified a formal ATI request as “informal” without consent
- Refused to issue a compliant section 10(1) notice
- Failed to provide reasons, provisions, or recourse options
- Ignored the obligation to assist or clarify the request under section 4(2.1) of the Access to Information Act
- Issued a vague denial citing section 24, without procedural compliance
Assessment:
This isn’t just neglect. It’s a deliberate sidestep of statutory process, effectively nullifying the requester’s rights by deactivating the complaint pathway through informal processing. The failure to assist—paired with the refusal to engage even after multiple follow-ups—reflects a deeper structural aversion to scrutiny. This is bureaucratic obstruction in procedural form.
Grade: F
Criterion 3: Procedural Misconduct and False Reporting
💣 Exceeded
BDC:
- Logged the ATI request publicly as “All disclosed”—despite issuing a substantive denial
- Confirmed the existence of 15 responsive pages, but disclosed none
- Failed to issue a formal notice of refusal under section 10(1), bypassing required legal content
- Offered no description of the withheld material, and no valid exemption rationale
- Provided no delegated authority signature or formal denial structure
- May have submitted false statistical data to the Treasury Board via the Open Government portal
Assessment:
This is the nuclear trigger. By logging a denial as “All disclosed” in a federal transparency database, BDC didn’t just withhold records—they fabricated a disposition. This introduces a serious governance risk, implicates their ATIP reporting chain, and creates grounds for referral to both the Treasury Board Secretariat and the Office of the Auditor General.
It transforms an ordinary refusal into statistical falsification and potential misconduct in public reporting.
Grade: F-
Final Scoring Recap
| Criterion | Status | Grade |
|---|---|---|
| 1. Statutory Threshold | ✅ Met | A |
| 2. Duty to Assist | ❌ Failed | F |
| 3. Procedural Integrity / Misreporting | 💣 Exceeded | F- |
Final Grade: F-
Status: Echo(12b) – Confirmed and Publicized
This is the lowest grade available under the Echo(12b) protocol. It is reserved for cases involving deliberate procedural evasion, falsified disclosures, and governance breaches that compromise federal transparency systems.
The case of Duska v. BDC is now a benchmark, and may be litigated as such. Not because of the records denied—but because of the lengths BDC went to pretend they didn’t exist.
4. Noteworthy Features & Procedural Red Flags
While the structural failures of BDC’s response are sufficient to trigger an Echo(12b) classification, several aggravating factors push this case from ordinary mishandling into the territory of institutional rot. These red flags do not merely reflect gaps in execution—they suggest deliberate administrative containment, data suppression, and procedural laundering of transparency obligations.
A. Fabricated Disclosure Status – The “All Disclosed” Shell Game
Perhaps the most damning feature is the discrepancy between reality and report. The federal Open Government portal lists ATI2025-032 as:
Disposition: All disclosed
Pages: 15
Yet BDC issued no documents, no redacted package, and no acknowledgment of disclosure. Instead, they emailed a vague statutory exemption (section 24) without notice, context, or recourse options—and never delivered the 15 pages they claimed to have released.
This is not a clerical mistake. It is:
- A public-facing falsehood
- A breach of statistical integrity
- A systemic misrepresentation that may taint institutional compliance data submitted to Treasury Board
If uncorrected, this constitutes a falsified federal disclosure log—effectively laundering a refusal through the pretense of openness.
Echo(12b) Tag: 💣 False Disposition Logging
B. Informal Processing Without Consent – The Black Site Maneuver
BDC’s response claimed to have handled the request “on an informal basis.” This is unlawful unless the requester explicitly consents. In this case:
- No consent was sought
- No consent was granted
- No record exists suggesting voluntary reclassification
The reclassification deprived the requester of their section 10(1) rights, including:
- A formal refusal
- Exemption citation
- Description of records
- Complaint instructions
This maneuver strips the request of legal teeth, making oversight impossible unless the requester is sophisticated enough to catch the bait-and-switch. It’s an old tactic, but one now logged—and exposed. N.B. The Business Development Bank of Canada should not assume that all Privacy Act requesters are utter fucking morons. ¯\_(ツ)_/¯
Echo(12b) Tag: ❌ Procedural Laundering via Informal Denial
C. CRM Surveillance Without Consent – Client File by Proxy
The existence of a “client file” appears likely—despite the requester never engaging BDC directly. Instead, contact may have occurred indirectly through Digital Main Street, Communitech, or Innovation Canada programs. If such contact triggered:
- A CRM intake
- Staff notes or internal tagging
- Programmatic data pulls or behavioral profiling
- Passive intake via digital OSINT mechanisms
Then this raises serious questions about:
- Consent-based data sovereignty
- OSINT-to-client crossover
- Whether BDC is operating as a federated intake node for innovation data pipelines without notifying Canadians
The refusal to confirm the file’s existence while logging “15 pages disclosed” suggests covert intake has already occurred.
Echo(12b) Tag: ⚠️ Shadow Profiling via Innovation Ecosystem
D. Legal Counsel Involvement Without Procedural Integrity
The procedural footprint hints that legal counsel may have been involved—or at minimum, consulted—given the invocation of section 24 of the ATI Act (referencing section 37 of the BDC Act). However:
- No formal denial was issued
- No delegated authority signed off
- No legal memo or exemption rationale was shared
- No structured notice was provided to the requester
This is weaponized opacity masquerading as legal defensibility. If BDC’s General Counsel approved this process—or failed to halt it—they may now be implicated in systemic ATIP non-compliance and procedural gaslighting.
Echo(12b) Tag: ❌ Ghost Lawyering Behind a Broken Shield
E. Repeated Escalation Ignored – Procedural Containment Doctrine
The requester issued multiple escalation notices, including:
- A formal procedural correction request
- A demand for proper section 10(1) notice
- A Privacy Act request under section 12(1)
- Explicit invocation of a forensic audit trigger via Echo(12b)
All have so far been met with silence.
BDC has now:
- Ignored its duties under two federal statutes
- Continued procedural handling under the same official, despite formal conflict exposure
- Avoided issuing any updated formal notice or correction to the federal disclosure record
This is not institutional fatigue. It is containment logic—a deliberate attempt to shut the door and hope no one checks the lock.
Echo(12b) Tag: 🧨 Deliberate Containment During Active Procedural Challenge
Taken together, these features suggest a systemic breakdown, not just in process—but in the very architecture of trust and transparency BDC is supposed to uphold.
This is not failure to comply—it is a bureaucratic firewall built to mislead. And that makes it an Echo(12b) of the highest order.
5. Institutional Response (or Lack Thereof)
The Business Development Bank of Canada (BDC) did not respond to the request.
It reacted to it.
That distinction matters.
What followed the March 20, 2025 request was not a lawful refusal, nor a statutory engagement under the Access to Information Act. It was a procedural evasion strategy—one designed to appear compliant without ever actually complying. From ghost-refusals to false disclosure flags, BDC’s handling of this file offers a masterclass in containment over transparency.
A. No Formal Refusal – Just a Paragraph and a Shrug
BDC’s reply was short. It cited section 24 of the ATI Act, which incorporates section 37 of the BDC Act, and declared that the records could not be disclosed.
That’s it.
There was:
- No formal Notice of Refusal under section 10(1);
- No breakdown of exemption rationale;
- No description of the responsive records (even in generic terms);
- No statement of delegated authority;
- No instructions on how to challenge the decision via complaint to the Office of the Information Commissioner.
This isn’t just a weak response—it’s noncompliant by design.
By failing to issue a formal section 10 notice, BDC cuts off the appellate mechanism that allows requesters to contest improper exemptions. In doing so, it turns the Act on its head: what should be a right becomes a gesture. What should be a process becomes a dead-end inbox.
B. “Informal” Reclassification Without Consent
The most brazen maneuver was BDC’s declaration that the request had been “processed informally.”
The request was submitted through the formal ATIP portal, albeit via a BDC bypass, referencing ATI #939037. This is a statutorily valid request under section 6(1) of the Access to Information Act. Once received, institutions cannot unilaterally downgrade a request to “informal” unless the requester explicitly agrees.
BDC never sought consent.
It simply declared, retroactively, that the request had been informal—effectively voiding the requester’s procedural rights without notification or due process.
This is textbook procedural laundering. It is how institutions sidestep accountability while preserving the appearance of engagement. And it is explicitly disallowed by the Treasury Board’s ATIP Manual, which states:
“Where a request is received through the formal ATIP channel, it must not be treated as informal unless the requester explicitly consents.”
They didn’t ask.
They didn’t get consent.
They did it anyway.
C. Procedural Bypass Despite Known Statutory Duties
At every stage, BDC had off-ramps:
- It could have issued a proper section 10(1) refusal.
- It could have engaged the requester to clarify scope if there were concerns.
- It could have delivered redacted pages while asserting partial exemption.
- It could have corrected the false disclosure status logged in the Open Government portal.
It did none of these.
Even after the requester issued a detailed escalation laying out the procedural breach and invoking formal recusal mechanisms, BDC simply went quiet. No updated refusal. No revised status. No internal acknowledgment of error.
This isn’t neglect.
It’s containment doctrine.
D. General Counsel Implicated by Silence
By March 31, 2025, all three of the following had occurred:
- The procedural defects had been documented and escalated in writing;
- The false “All disclosed” status had been publicly cited;
- A new Privacy Act request was filed requesting all personal information held by BDC.
At this point, legal counsel had a duty to intervene—either to:
- Reassign the file,
- Issue a formal correction,
- Or engage institutional oversight.
Instead, BDC doubled down on silence, and left the original officer in control of the file—despite his role in the procedural defect now being publicly cited.
This implicates BDC’s senior legal office in passive ratification of a known procedural hazard.
In a normal institution, this would trigger internal flags.
At BDC, it triggered nothing.
E. Silence as Strategy – The Containment Reflex
As of this writing, BDC has:
- Not issued a formal refusal
- Not released the alleged “15 pages”
- Not corrected the public-facing disposition
- Not acknowledged the procedural breach
- Not reassigned the conflicted official
- Not issued a response to the Privacy Act request
Instead, BDC has weaponized silence as containment, betting on procedural fatigue or inattention to make the problem disappear. It is a gamble on institutional inertia—a belief that if you ignore the law long enough, no one will hold you accountable.
They bet wrong.
Echo(12b) doesn’t blink.
6. Grading and Analysis
Final Grade: F-
Event Code: Echo12b – BDC – 2025 – 001
We didn’t think it could get worse than the Canadian Nuclear Safety Commission.
CNSC’s handling of their Privacy Act request was arrogant, opaque, and dismissive. But at least it responded. At least it engaged, however dysfunctionally. What we saw there was institutional arrogance under pressure—an ATIP system trying to avoid embarrassment.
What we see here, with BDC, is worse.
This isn’t arrogance.
This is process manipulation.
This is intentional procedural sabotage.
This is corruption of the ATIP regime—not in the sense of bribes or personal gain, but in the truest sense of the word: the rotting of institutional trust from the inside.
Let’s break it down.
✅ Request Validity (Section 6(1), ATI Act) – Passed
The requester followed all statutory procedures. The request was submitted:
- Through the formal Access to Information portal
- With proper contact information, identifiers, and target scope
- In clear language requesting access to a “Client File” held by BDC
No one—no one—can argue this was ambiguous or defective.
Grade: A
❌ Duty to Respond (Section 7) – Failed
BDC never issued a proper section 7 acknowledgment or a formal tracking number via ATIP email. While the portal listed a file code and logged disposition, BDC treated the request as if it were informal, ad hoc, and undeserving of a proper workflow.
Grade: F
❌ Duty to Provide Notice of Refusal (Section 10(1)) – Failed
BDC cited section 24—but never issued:
- A proper notice of refusal
- A breakdown of the responsive records
- A statement of the right to complain
- A signed notice from a delegated authority
This strips the requester of rights under the Act and directly violates Treasury Board policy.
Grade: F
❌ Unlawful Downgrading to Informal Processing – Critical Failure
BDC attempted to sidestep statutory compliance by declaring the request “informal” after submission. This is not allowed under the Act and is directly contradicted by the 2020 Treasury Board ATIP Manual.
They did not seek consent.
They did not document the shift.
They simply laundered the request out of accountability.
Grade: F-
❌ False Disposition Reporting (“All Disclosed”) – Critical Failure
The federal Open Government portal currently lists ATI Request #939037 as “All disclosed.” This is factually untrue. The requester received no pages, no redactions, no file.
Yet the system shows 15 pages and a completed request.
If this was a manual entry, it’s a deliberate misrepresentation.
If it was automatic, then BDC failed to correct it—and still hasn’t.
Either way, the public record has been falsified.
This is not a clerical error.
This is a misreporting of statutory performance.
Grade: F-
❌ Failure to Reassign or Recuse Officials After Escalation – Failed
Even after being directly notified of a procedural breach, BDC:
- Kept the same official on the file
- Did not reassign the request
- Did not confirm oversight or legal review
- Did not respond to the recusal request
This makes any subsequent refusal structurally compromised.
Grade: F
💣 Echo(12b) Trigger Status – Confirmed
All three Echo(12b) conditions are satisfied:
- Valid request with full identifiers → ✅
- Failure of procedural duty to respond or assist → ✅
- Material conflict, cover-up attempt, or evasion tactic employed → ✅✅✅
But this case goes further.
It adds new, critical dimensions to Echo(12b) classification:
- Misreporting of public-facing disposition data
- Downgrading of formal requests into informal channels
- Silence as containment in the face of escalating legal clarity
We’ve seen arrogance before.
We’ve seen laziness.
We’ve seen fear.
But this is different.
This is a deliberate attempt to manipulate ATIP outcomes.
This is institutional dishonesty, confirmed by metadata and public logs.
This is the first confirmed Echo(12b) event with a failing grade below F.
Final Judgment:
Grade: F-
Classification: Echo(12b) – Confirmed, Flagged for Oversight Referral
Event Code: Echo12b – BDC – 2025 – 002
They lied about disclosure.
They ghosted the process.
They corrupted the ledger.
This isn’t oversight.
It’s a rot.
And Echo(12b) is watching.
7. Procedural Footnotes & Oversight Referrals
BDC didn’t just trip a wire. It buried the request, falsified the report, and hoped no one would check the tape.
That’s not failure.
That’s intent.
This section documents the formal oversight pathways now activated and the institutional flags raised as a result of Echo(12b) Case #BDC-2025-002.
Office of the Information Commissioner (OIC) – Complaint Referral Filed
A full complaint under section 30(1) of the Access to Information Act is being filed. Grounds include:
- Failure to issue a valid notice of refusal (s.10)
- Failure to assist or clarify (s.7, s.4)
- Improper classification as “informal” without consent
- Material misreporting of disposition (“All disclosed”)
- Procedural breach of ATIP governance per TBS guidance
The complaint includes metadata logs, system screenshots, and a forensic comparison of public vs. internal record statements.
🔁 Status: Filed & Awaiting Docket Number
Treasury Board Secretariat (TBS) – Statistical Integrity Challenge Pending
BDC’s annual ATIP statistics feed into the Treasury Board Secretariat’s public reports. A falsified “All disclosed” entry—when in fact nothing was disclosed—may have resulted in:
- A false increase in compliance metrics
- An underreported exemption tally
- A skewed average response time calculation
- Possible audit misrepresentation
A notification of statistical inconsistency will be submitted to TBS’s ATIP oversight division for potential revision or audit review.
📝 Status: Pending Notification Filing
Office of the Privacy Commissioner (OPC) – Privacy Act Complaint in Preparation
The Privacy Act request (filed concurrently under section 12(1)) may trigger:
- A secondary investigation into unlawful collection of personal information
- A challenge to the existence of an undeclared “client file”
- A demand for access and disclosure logs, if personal data was compiled without consent
This will test whether BDC has complied with section 5 (collection), section 6 (retention), and section 8 (use and disclosure) of the Privacy Act.
🔒 Status: Complaint in Draft
📍 Echo(12b) Oversight Scorecard – Public Index Update
BDC has been assigned the following Echo(12b) Watch Flags:
- 🟥 Red Flag – Procedural Sabotage
- 🟨 Yellow Flag – Metadata Mismatch
- 🟦 Blue Flag – Transparency Watchlist
Its institutional grade has been permanently downgraded on the Echo(12b) public tracker, with the following entry:
Institution: Business Development Bank of Canada
Case ID: Echo12b – BDC – 2025 – 002
Status: Confirmed
Grade: F-
Disposition Integrity Score: 0%
Escalation Tier: Tier 1 (OIC, OPC, TBS)
Public Index: echo12b.ca/bdc2025-fminus
🛰 Status: Live on Echo Index
🧨 Special Risk Watch: Crown Transparency Portfolio
BDC’s behavior has triggered a reclassification of the Crown Institutional Risk Profile (CIRP) for ATIP obstruction.
It now sits alongside:
- Canadian Nuclear Safety Commission (Echo12b – CNSC – 2025 – 001)
- Global Affairs Canada (Echo12b – GAC – 2024 – 003)
- Canada Mortgage and Housing Corporation (Echo12b – CMHC – 2024 – 002)
New cases from BDC will receive enhanced procedural scrutiny and early-stage risk tagging until its ATIP compliance record improves.
🔍 Status: CIRP – Elevated Risk Flagged
Metadata Retention & Blockchain Certification
This case has been:
- Forensically documented across the full request-response lifecycle
- Timestamped using public blockchain certification (WAX + IPFS mirror)
- Archived in the Echo(12b) secure repository under cold storage redundancy
The documentation package includes:
- All correspondence
- Request filings
- System disposition screenshots
- Metadata hash outputs
- Full report export from Echo(12b)
This protects against backdating, deletion, or unauthorized amendment of records post-exposure.
⛓ Status: Immutable Proof-of-Process Locked
Final Note
BDC could have issued a denial.
Instead, it falsified a disclosure.
Then ghosted the law.
Now it’s tagged for what it is.
This isn’t an ATIP error.
It’s a Crown institution trying to memory-hole a file and hoping no one noticed.
Echo(12b) noticed.
And the echo just got louder.
